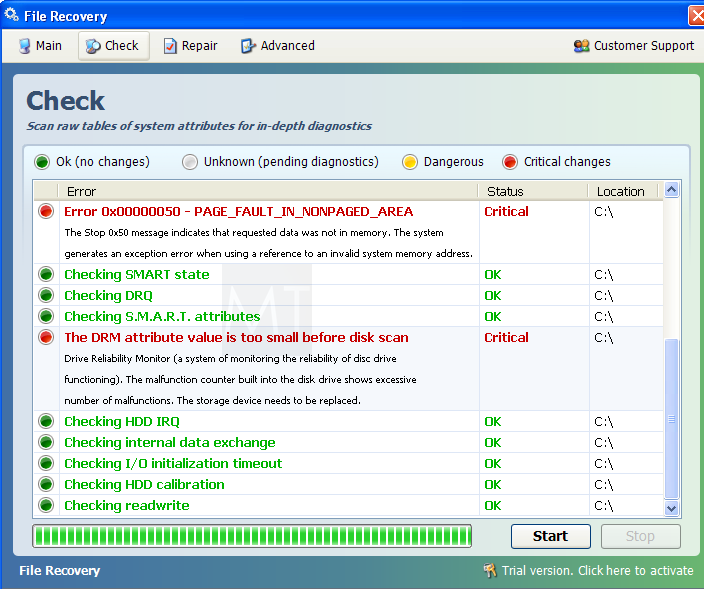
Program Files Empty Malware
Solved mrtstub. exe is not malware or virus and you may delete it safely. Concern You find a suspicious folder on your computer or removable hard drive which is a long string of numbersletters and the folder contains the files mrtstub. These files are the leftovers from when the Microsoft Malicious Software Removal Tool was run. Normally the folder is deleted automatically, but if the program was stopped in the middle of running or due to some other unexpected system behavior the files may remain behind. You can delete this folder files. For more information, see Microsofts article on the subject. In particular the section which states How to remove the Malicious Software Removal Tool. The Malicious Software Removal Tool does not use an installer. Typically, when you run the Malicious Software Removal Tool, it creates a randomly named temporary directory on the root drive of the computer. This directory contains several files, and it includes the Mrtstub. Mike Fahey. Kotaku elder, lover of video games, toys, snacks and other unsavory things. Complete list of types of malware along with all Cyber terminologies explained with examples and proper classification. What it is and How it attacks Users Manual. FreeFixer is a general purpose removal tool which will help you to delete potentially unwanted software, such as adware, spyware, trojans, viruses and. How to Remove Windows System Defender Malware. This wikiHow teaches you how to uninstall and remove completely the System Defender malware program from your Windows. Most of the time, this folder is automatically deleted after the tool finishes running or after the next time that you start the computer. Plant Anatomy An Applied Approach. However, this folder may not always be automatically deleted. In these cases, you can manually delete this folder, and this has no adverse effect on the computer. Folder-virus-file-recovery-2.jpg' alt='Program Files Empty Malware' title='Program Files Empty Malware' />
Computer virus Wikipedia. A computer virus is a type of malicious software program malware that, when executed, replicates itself by modifying other computer programs and inserting its own code. Infected computer programs can include, as well, data files, or the boot sector of the hard drive. When this replication succeeds, the affected areas are then said to be infected with a computer virus. Virus writers use social engineeringdeceptions and exploit detailed knowledge of security vulnerabilities to initially infect systems and to spread the virus. The vast majority of viruses target systems running Microsoft Windows,567 employing a variety of mechanisms to infect new hosts,8 and often using complex anti detectionstealth strategies to evade antivirus software. Motives for creating viruses can include seeking profit e. Computer viruses currently cause billions of dollars worth of economic damage each year,1. In response, free, open source antivirus tools have been developed, and an industry of antivirus software has cropped up, selling or freely distributing virus protection to users of various operating systems. Logan Watch Bluray Online 2017. As of 2. 00. 5, even though no currently existing antivirus software was able to uncover all computer viruses especially new ones, computer security researchers are actively searching for new ways to enable antivirus solutions to more effectively detect emerging viruses, before they have already become widely distributed. The term virus is also commonly, but erroneously, used to refer to other types of malware. A computer virus is a type of malicious software program malware that, when executed, replicates itself by modifying other computer programs and inserting its own. I have two of these directories empty and a third with the exact files you described they are only on my external hard drive. However I have never run the. Free Download Fast Empty Folder Finder 0. Locate and remove empty directories from your computer. On visiting a infected Website, this rogue uses a variety of animated images to simulate an online scan that fraudulently claims to find many nonexistent malware on. Thanks, but I managed to fix it. Turned out to be a conflicting program in the startup services. My recycle bin issue turns out to be slow at deleting files, even. Fast, affordable automatic website malware removal. Clean your website now. Malware encompasses computer viruses along with many other forms of malicious software, such as computer worms, ransomware, spyware, adware, trojan horses, keyloggers, rootkits, bootkits, malicious Browser Helper Object BHOs and other malicious software. The majority of active malware threats are actually trojan horse programs or computer worms rather than computer viruses. Windows 2008 Activator Daz more. The term computer virus, coined by Fred Cohen in 1. Viruses often perform some type of harmful activity on infected host computers, such as acquisition of hard disk space or central processing unit CPU time, accessing private information e. However, not all viruses carry a destructive payload and attempt to hide themselvesthe defining characteristic of viruses is that they are self replicating computer programs which modify other software without user consent. Historical developmenteditEarly academic work on self replicating programseditThe first academic work on the theory of self replicating computer programs1. John von Neumann who gave lectures at the University of Illinois about the Theory and Organization of Complicated Automata. The work of von Neumann was later published as the Theory of self reproducing automata. In his essay von Neumann described how a computer program could be designed to reproduce itself. Von Neumanns design for a self reproducing computer program is considered the worlds first computer virus, and he is considered to be the theoretical father of computer virology. In 1. 97. 2, Veith Risak, directly building on von Neumanns work on self replication, published his article Selbstreproduzierende Automaten mit minimaler Informationsbertragung Self reproducing automata with minimal information exchange. The article describes a fully functional virus written in assembler programming language for a SIEMENS 4. In 1. 98. 0 Jrgen Kraus wrote his diplom thesis Selbstreproduktion bei Programmen Self reproduction of programs at the University of Dortmund. In his work Kraus postulated that computer programs can behave in a way similar to biological viruses. First examplesedit. The Mac. Mag virus Universal Peace, as displayed on a Mac in March 1. The Creeper virus was first detected on ARPANET, the forerunner of the Internet, in the early 1. Creeper was an experimental self replicating program written by Bob Thomas at BBN Technologies in 1. Creeper used the ARPANET to infect DECPDP 1. TENEX operating system. Creeper gained access via the ARPANET and copied itself to the remote system where the message, Im the creeper, catch me if you can was displayed. The Reaper program was created to delete Creeper. In fiction, the 1. Michael Crichtonsci fi movie Westworld made an early mention of the concept of a computer virus, being a central plot theme that causes androids to run amok. Alan Oppenheimers character summarizes the problem by stating that. To which the replies are stated Perhaps there are superficial similarities to disease and, I must confess I find it difficult to believe in a disease of machinery. Crichtons earlier work, the 1. The Andromeda Strain and 1. In 1. 98. 2, a program called Elk Cloner was the first personal computer virus to appear in the wildthat is, outside the single computer or computer lab where it was created. Written in 1. 98. Richard Skrenta while in the ninth grade at Mount Lebanon High School near Pittsburgh, it attached itself to the Apple DOS 3. This virus, created as a practical joke when Skrenta was still in high school, was injected in a game on a floppy disk. On its 5. 0th use the Elk Cloner virus would be activated, infecting the personal computer and displaying a short poem beginning Elk Cloner The program with a personality. In 1. Fred Cohen from the University of Southern California wrote his paper Computer Viruses Theory and Experiments. It was the first paper to explicitly call a self reproducing program a virus, a term introduced by Cohens mentor Leonard Adleman. In 1. 98. 7, Fred Cohen published a demonstration that there is no algorithm that can perfectly detect all possible viruses. Fred Cohens theoretical compression virus3. However, antivirus professionals do not accept the concept of benevolent viruses, as any desired function can be implemented without involving a virus automatic compression, for instance, is available under the Windows operating system at the choice of the user. Any virus will by definition make unauthorised changes to a computer, which is undesirable even if no damage is done or intended. On page one of Dr Solomons Virus Encyclopaedia, the undesirability of viruses, even those that do nothing but reproduce, is thoroughly explained. An article that describes useful virus functionalities was published by J. B. Gunn under the title Use of virus functions to provide a virtual APL interpreter under user control in 1. The first IBM PC virus in the wild was a boot sector virus dubbed cBrain,3. Farooq Alvi Brothers in Lahore, Pakistan, reportedly to deter unauthorized copying of the software they had written. The first virus to specifically target Microsoft Windows, Win. Vir was discovered in April 1. Windows 3. 0. 3. 8 The virus did not contain any Windows APIcalls, instead relying on DOS interrupts. A few years later, in February 1. Australian hackers from the virus writing crew VLAD created the Bizatch virus also known as Boza virus, which was the first known virus to target Windows 9. In late 1. 99. 7 the encrypted, memory resident stealth virus Win. Cabanas was releasedthe first known virus that targeted Windows NT it was also able to infect Windows 3. Windows 9x hosts. Even home computers were affected by viruses. The first one to appear on the Commodore Amiga was a boot sector virus called SCA virus, which was detected in November 1.